A Self-Hosted VPN Solution

OpenVPN is probably one of the most popular Open Source VPN products available (not that I know actual figures, I’m just going off how often its name comes up), but the product lacks an easy management tool to connect clients and keep an eye on things.
Well, they do offer the Access Server product, but it costs money. Not a whole lot of money (min USD$96/year), but its still a lot for someone who just wants to be able to connect to their home network from anywhere.
So I’ve been on the hunt now for a easy-to-manage VPN product for personal use. I don’t want to host it in the cloud, I just want to use an existing machine in my home network and go from there.
Microsoft Remote Access
Out of the box, Microsoft let you turn any Windows Server 2012 (and earlier) server into a fully featured VPN server. In fact, if you do what I did and enable the Server Essentials feature, this will be enabled and configured for you automatically. I had surprising instantaneous success connecting a Windows machine to my VPN using the native VPN client capability. But, I couldn’t for the life of me get a Mac to connect to it.
Disclaimer: I’m not savvy with networking or VPN protocols yet, so this is just some dude blundering along trying to get stuff working. Take this post with a grain of salt. If you know what you’re doing, please share your knowledge.
After tweaking settings on the Remote Access feature, forwarding ports, opening firewalls, etc. I gave up and decided to look for alternatives.
SoftEther VPN
The hunt for an alternative unearthed the SoftEther VPN Project. Install the product on a server and you can then connect instances of their client application to it.
It’s a fantastic product, and it supports every common VPN protocol with just a few clicks.
There isn’t really a stable OSX client yet though, in fact if you try to download it they don’t recommend using it. I tried to set up a L2TP VPN with the product to get my Mac connected, but again I couldn’t and just gave up and kept looking for alternatives.
Pritunl
This product is where I’ve landed now. It’s name came up on some Reddit discussions, and it really is a simple product to use. It’s open source and free (well, if you only want to have a single VPN server), and they publish packages for installation on Linux.
At a basic level, it’s just a fancy wrapper around OpenVPN, but it really requires little knowledge or critical thinking to get up and running, which really appeals to me.
Installing Pritunl
If you install on Ubuntu Server, then the instructions they provide are great. Installing on CentOS 7 though didn’t work straight away though, because MongoDB didn’t install itself as a dependency. Here’s what I did to install it (from a fresh install of CentOS 7 Minimal), adding in the MongoDB 3 install before the pritunl install:
1 | touch /etc/yum.repos.d/pritunl.repo |
AFAIK MongoDB 3 is required, which is why we’re not installing the provided package in the EPEL repository.
Also, I’ve opened up ports 9700/tcp and 443/udp. 9700 is the default admin interface port, but the pritunl product will generate a port to use for the VPN when you configure the server (I think its randomly) which I change to 443. Some routers (hotels, cafes, etc.) will block ports other than 80 and 443, so this will allow you to still connect to your VPN over those networks. I didn’t really need to change it, as the port is forwarded from my router anyway, but it’s just how I did it anyway (also note that your client config will need to change if you’re forwarding to a different port).
It’s as simple as adding an Organisation and a User:
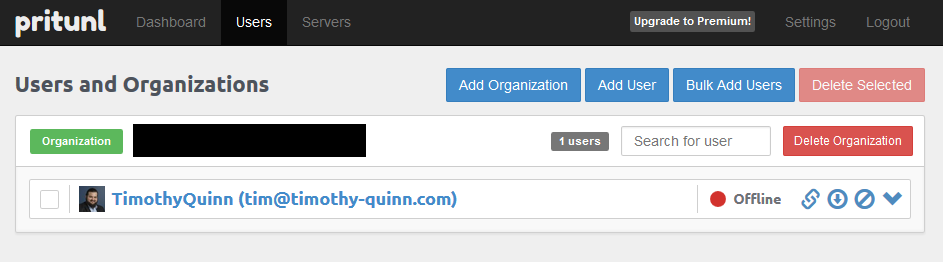
And then configuring the server against the organisation:
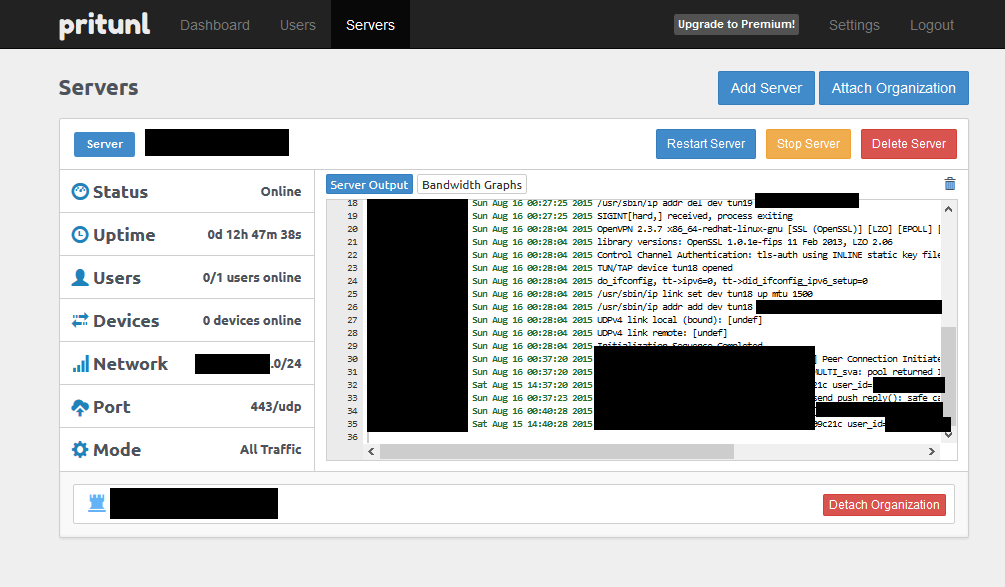
To connect clients, you just need to download the Pritunl client software from their website and download the configuration for the individual user from the Users page (the little download icon next to the user’s name) and load it into the client:

Now I can happily access my home network from both Mac and PC, and it seems to automatically route between the subnet it creates and the subnet of my home network as well.